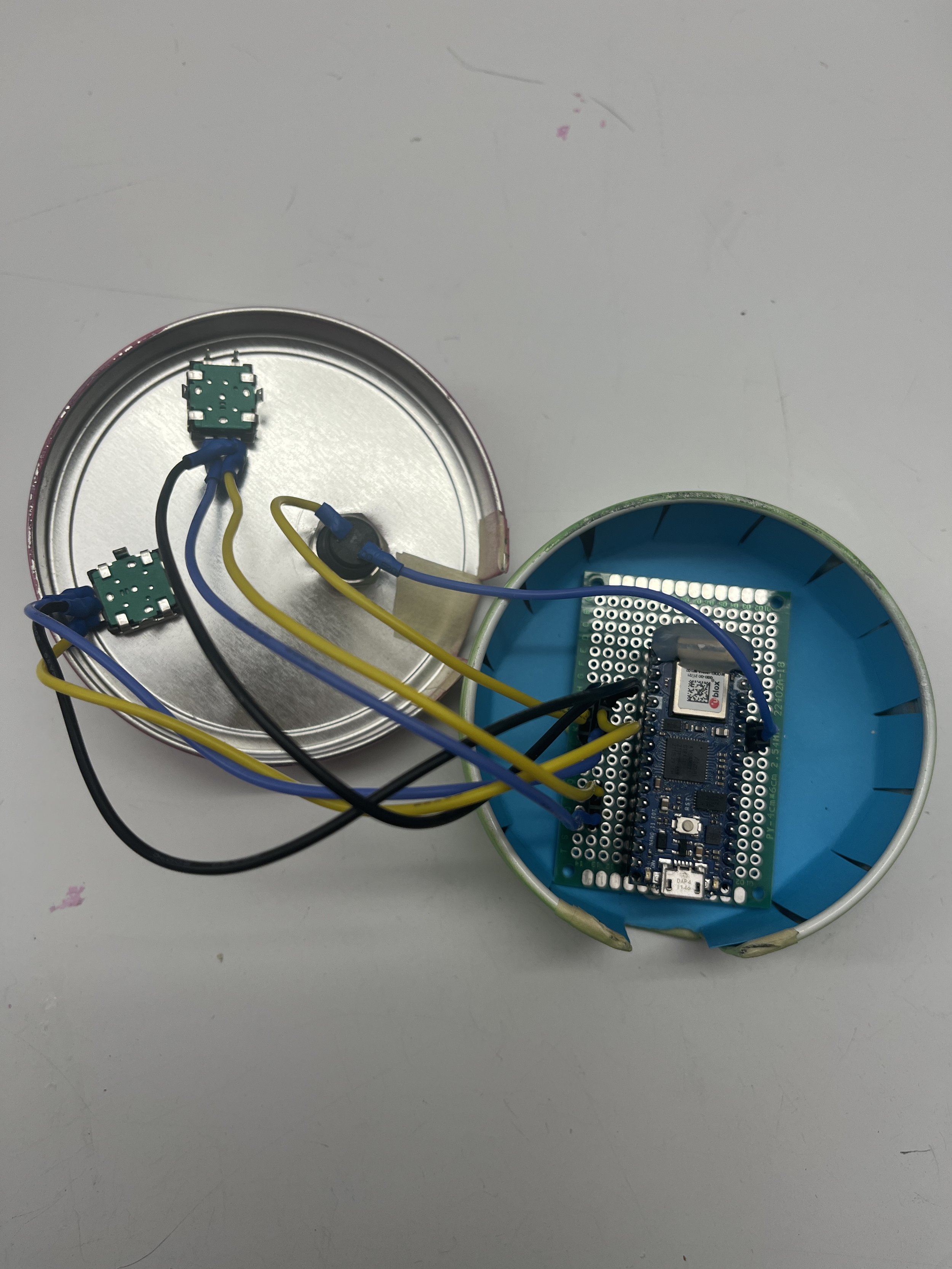
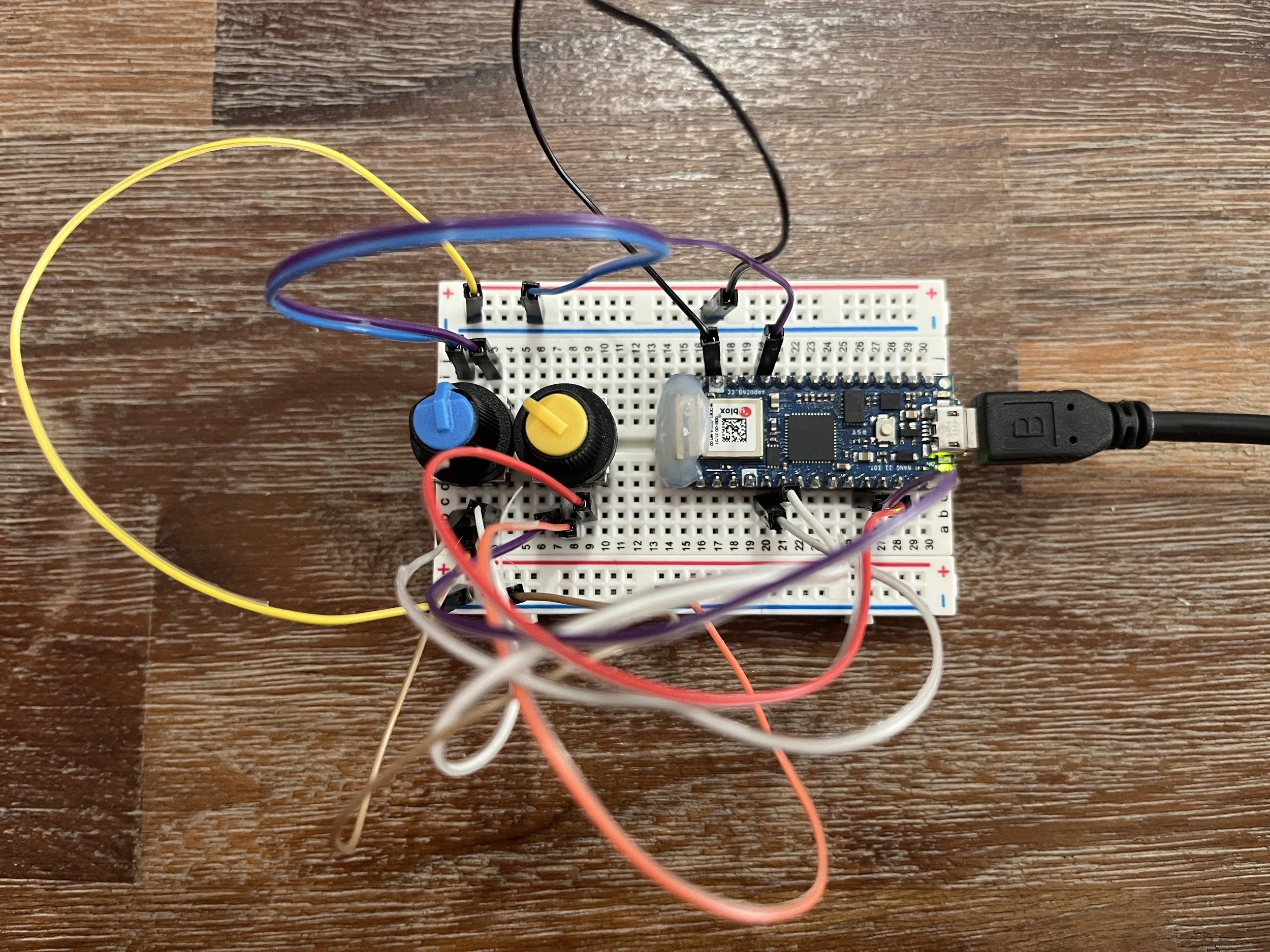
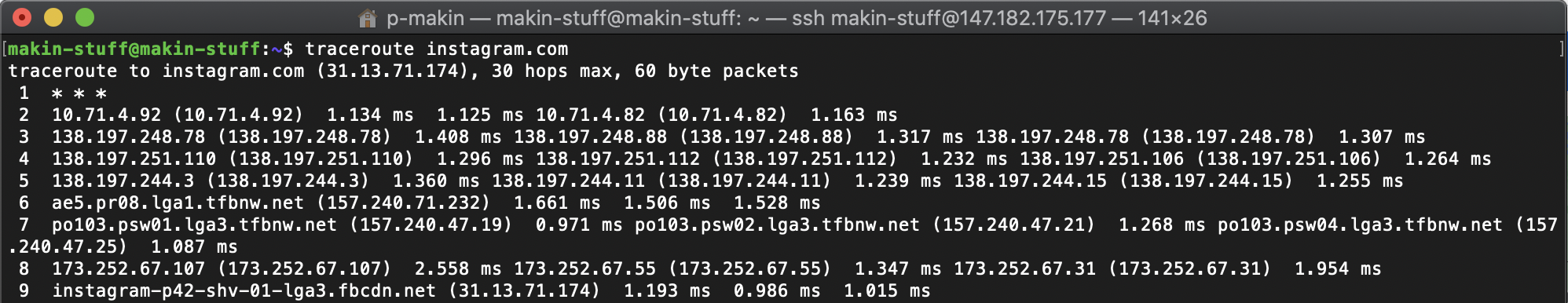
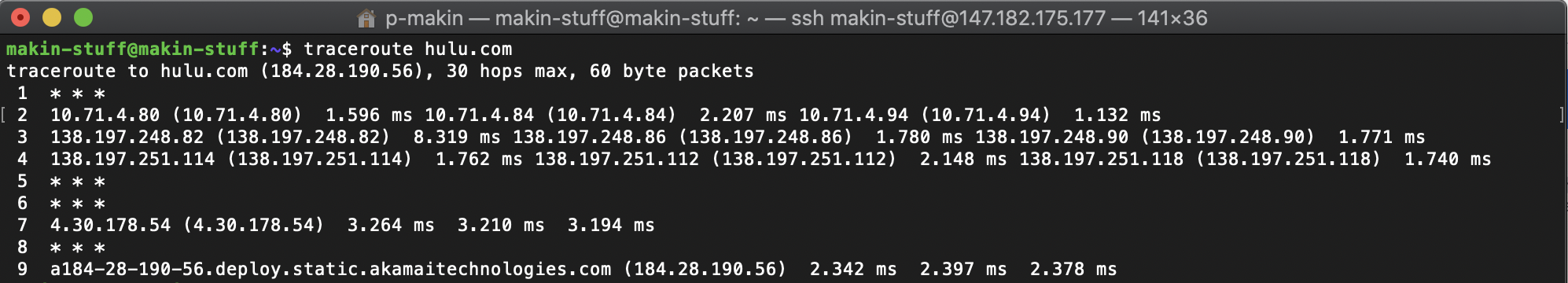
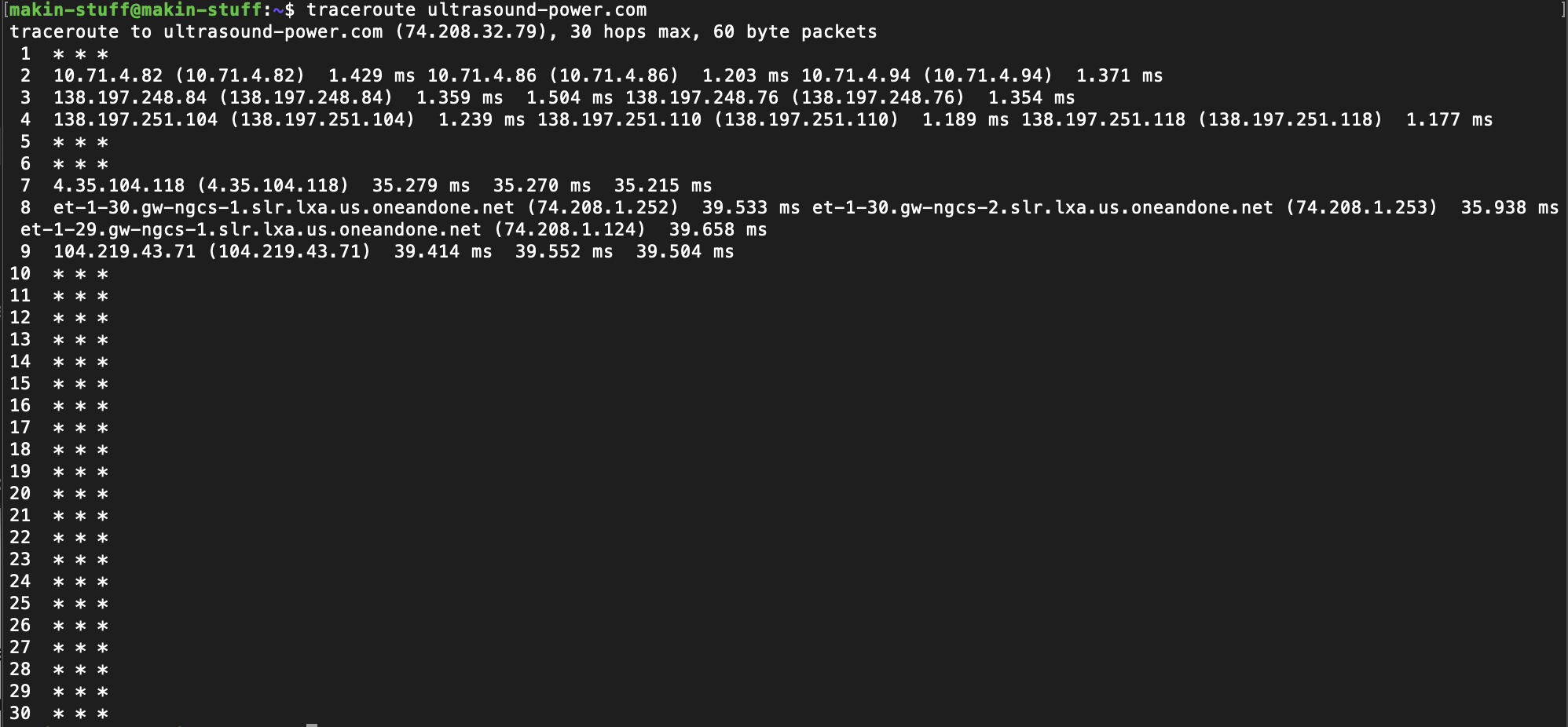
Sadly, Tom’s “Understanding Networks” class is coming to a close. I looked over my notes from the semester and here are my key takeaways:
In tech vulnerability is a weakness but in art vulnerability is valuable
The internet is PUBLIC space
I’m anti- smart-ifying the unnecessary
On the technical side:
The client makes the request, the server responds to the request
Open System Interconnections model (layers of the internet?!)
| Application | HTTP |
| Presentation | Unicode |
| Session | ICP |
| Transport | TCP / UDP |
| Network | IP |
| Data Link | WiFi / GSM |
| Physical | WiFi / GSM |
Left over questions and concerns:
What projects can I build with what I learned in class? I want to learn to collect my own MQTT data and do something with it!
What are the implications of networks as large as the internet? Can it be accessible to all? And if not, to whom?
What data gets prioritized on the internet? What information can we be certain is true? What happens to our data?
What is digital colonialism and can net neutrality actually be achieved?
If we are unhappy with how the internet currently works, who has the power to change it?
What takes more energy: networks based on cables or networks sustained by satellites? Which impacts the world more negatively?